The free tier of VMware Aria Hub was accounced VMware Explore back in November and I recently got access. This blog post covers the three steps required to get an AWS account connected and explores how we can start to query the inventory data.
The free tier allows you to connect up to two public cloud accounts from either Azure or AWS and there is no reliance on other VMware products or services, so this allows you to sign-up and experience how VMware Aria Hub powered by VMware Aria Graph can simplify the complexity of multi-cloud management.
#Data Source Setup
The very first step before we onboard our account is to access the service. Login to https://console.cloud.vmware.com and launch the VMware Aria Hub service.
Select your data source, in this post we will be using AWS.
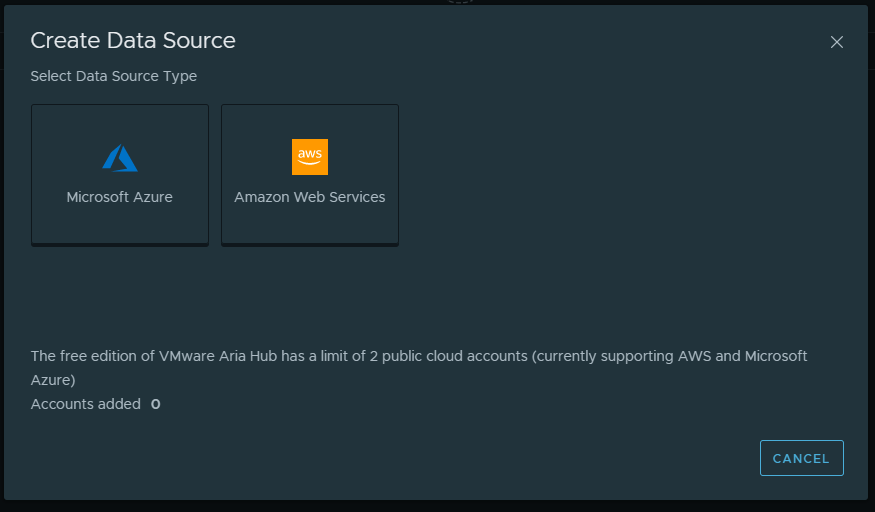
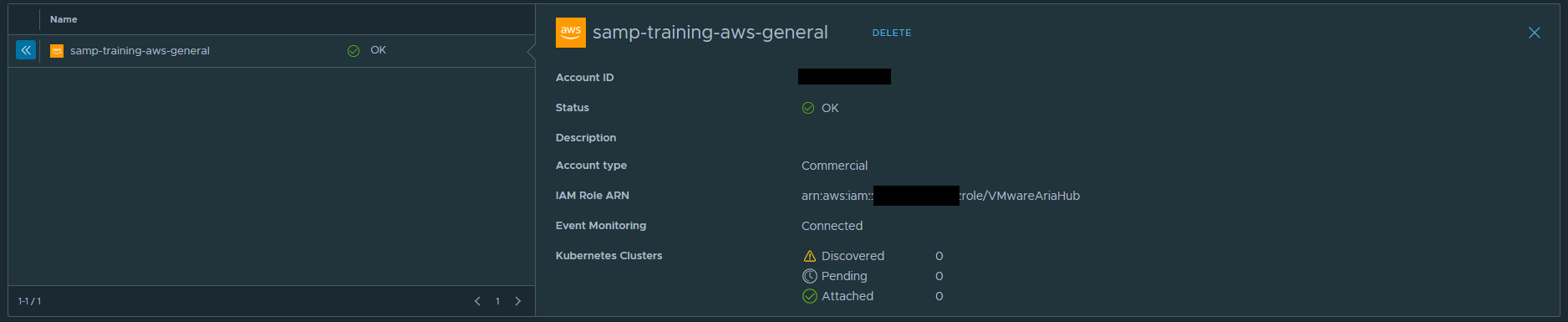
Provide a name and the AWS Account ID that you are connecting to.
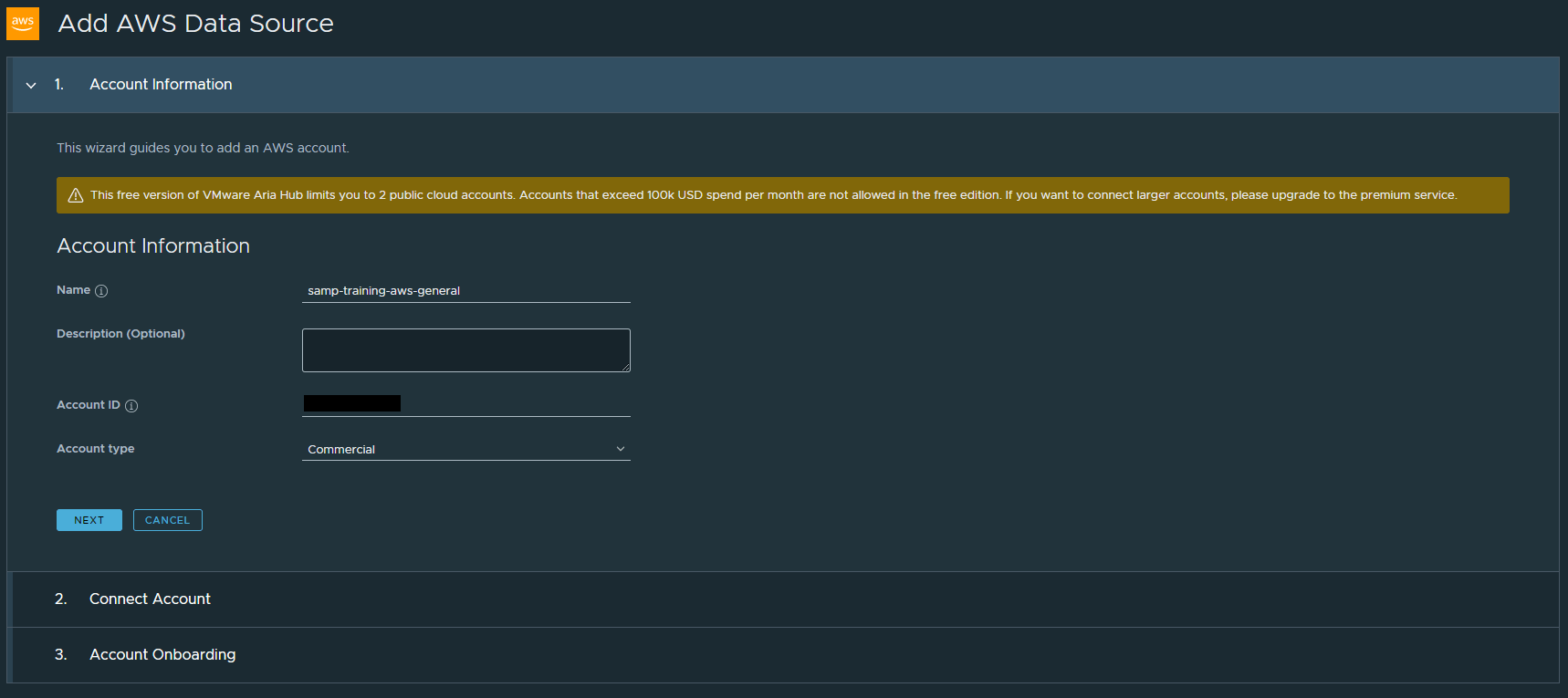
Step 2 includes some steps to configure an IAM Role that will allow VMware Aria Hub to connect to our AWS account.
If you click the CREATE AWS IAM ROLE FOR VMWARE ARIA button it will open in a new window and auto populate the Account ID and External ID. The Account ID that is provided in this step is an external account.
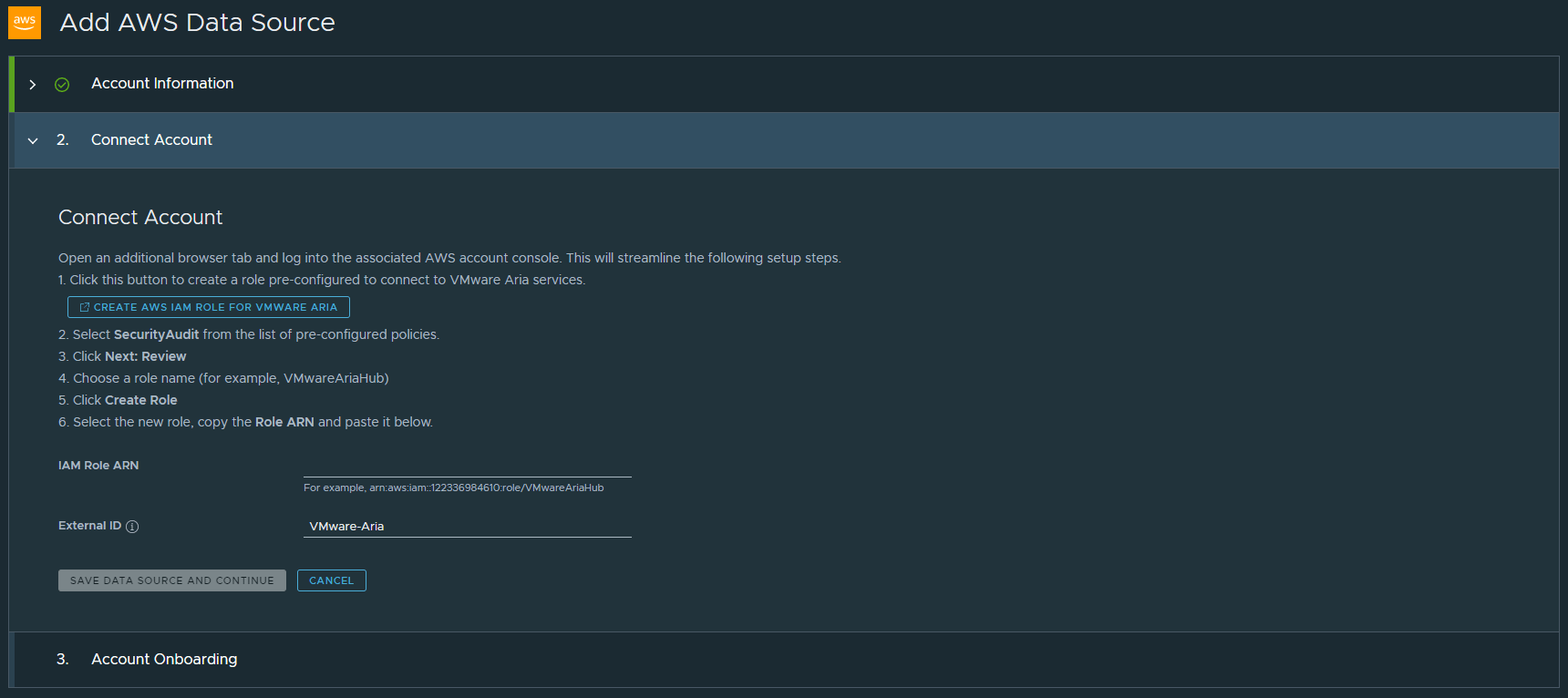
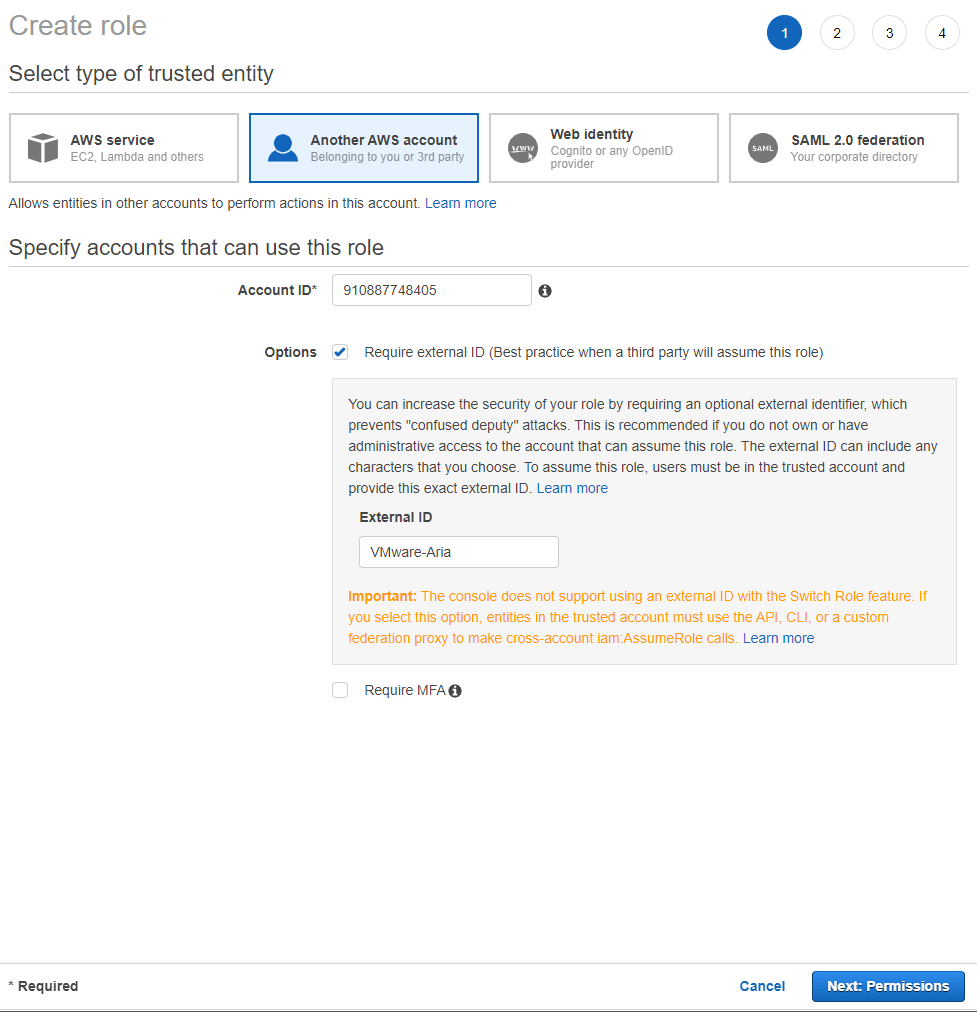
We need to specifically attach the SecurityAudit policy to our new role.
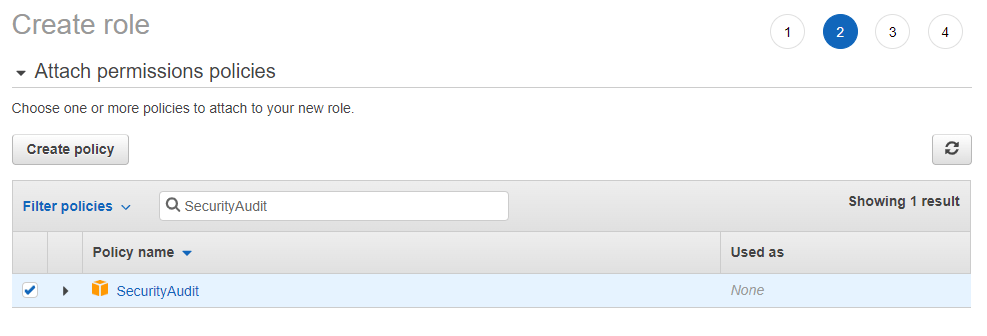
No tags are required, but add them if your organisation uses them.
Provide a name for your new role, I have used VMwareAriaHub. Make not of this role name as you will need it in a later step.
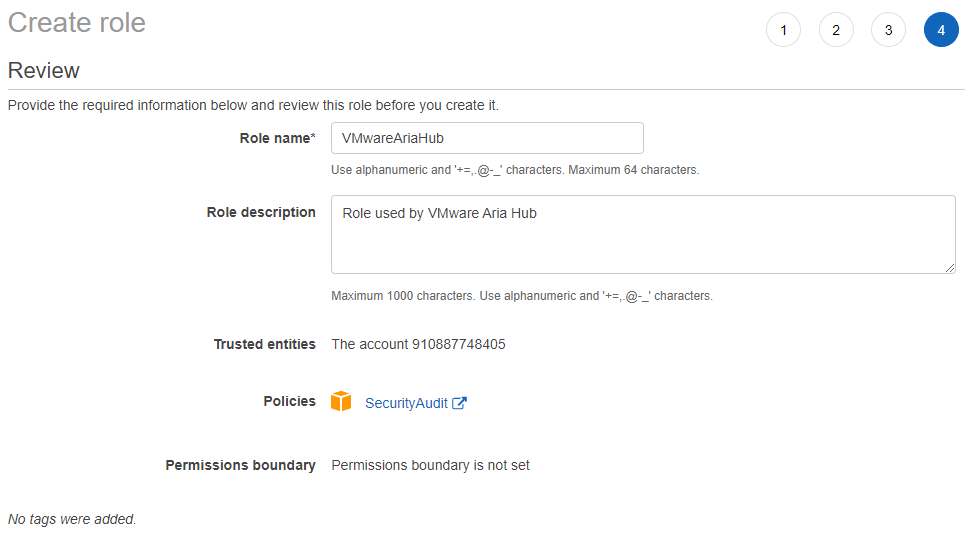
Once the role has been created, select it and make note of the ARN.
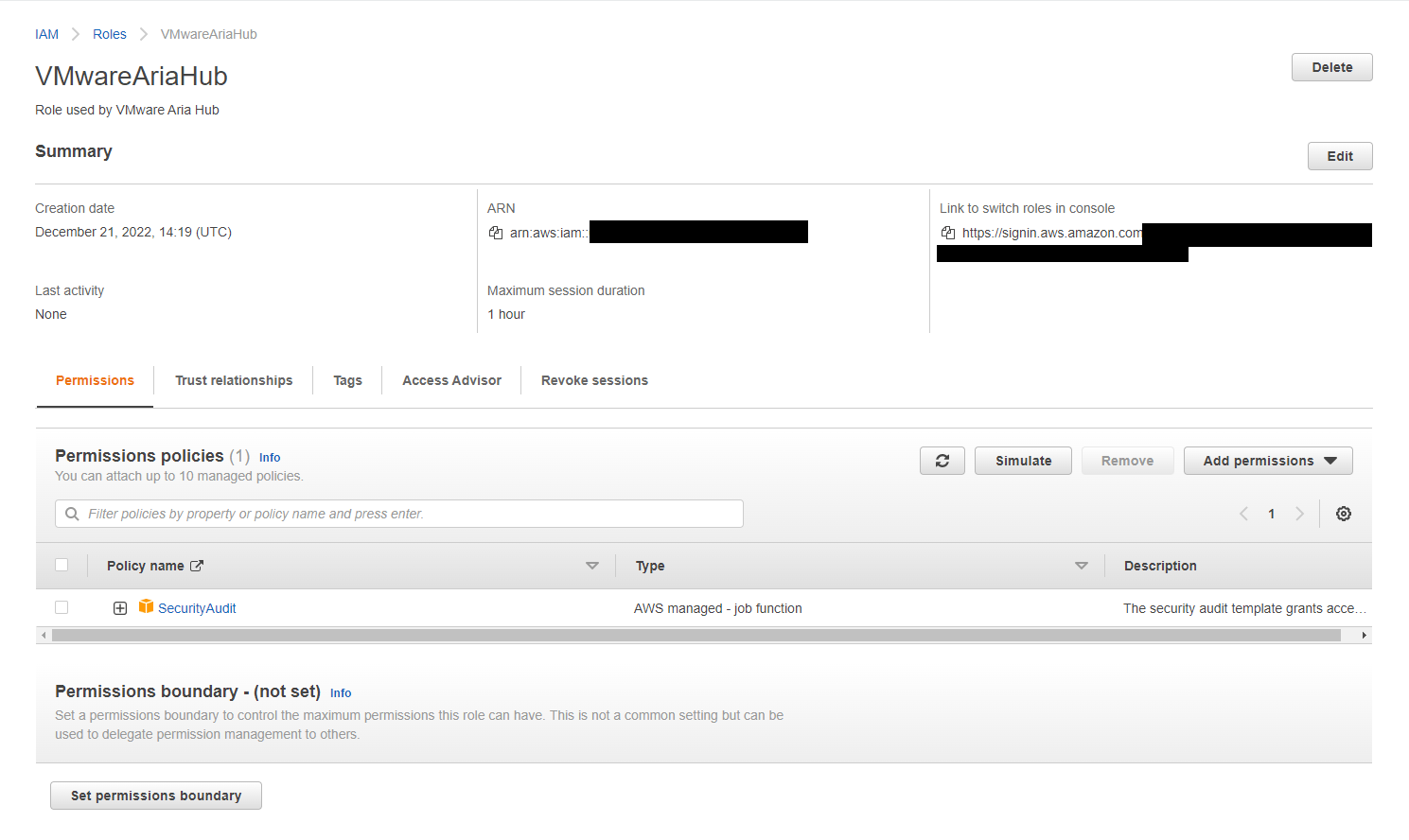
Paste the ARN value into the IAM Role ARN field in the Aria Hub portal. The External ID value should match the one you used when creating the IAM Role.
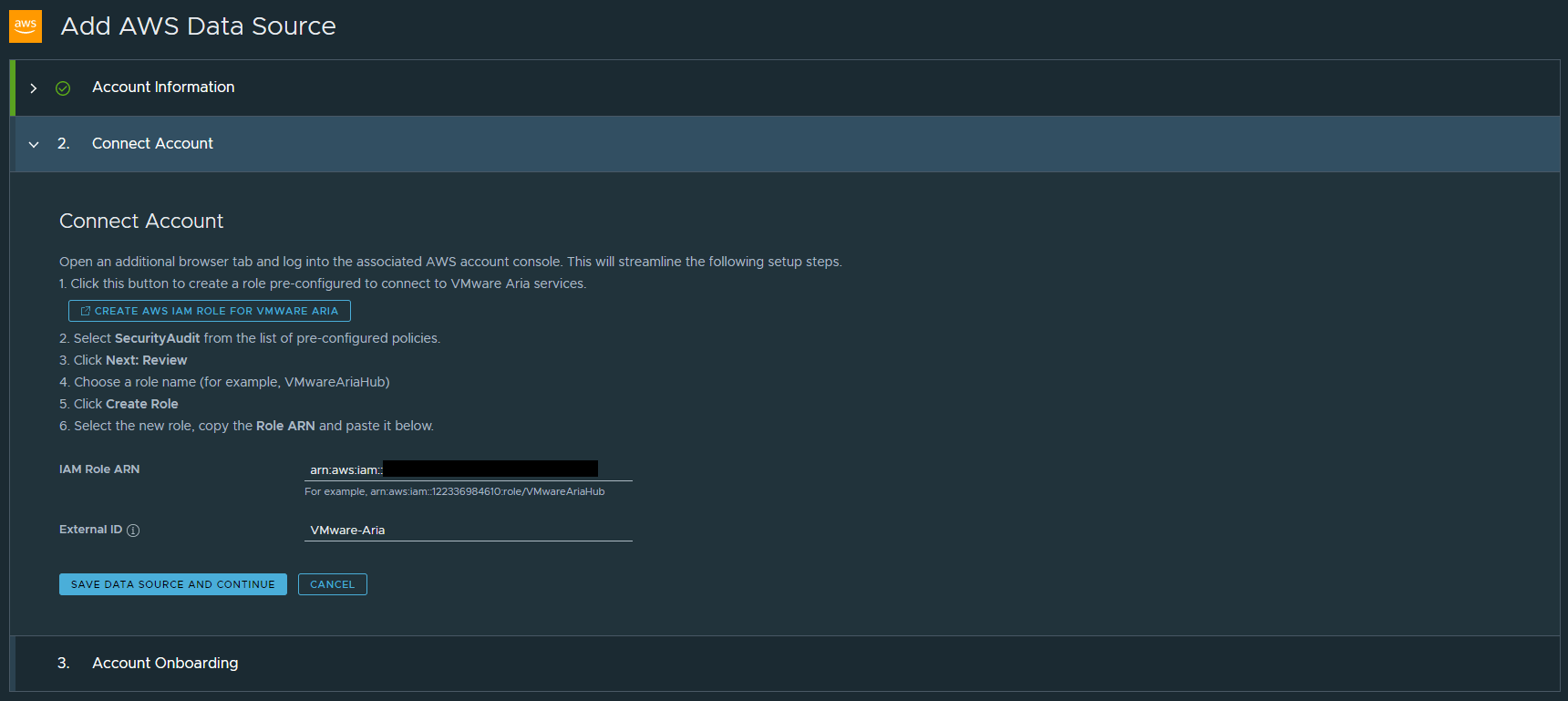
This is the final step for onboarding our account and it is asking us for a couple of things
- Enable CloudTrail in AWS for event monitoring purposes (we wont cover this step, but find CloudTrail and follow the steps to enable).
- Run a script to configure an Event Stream stack that utilises CloudFormation.
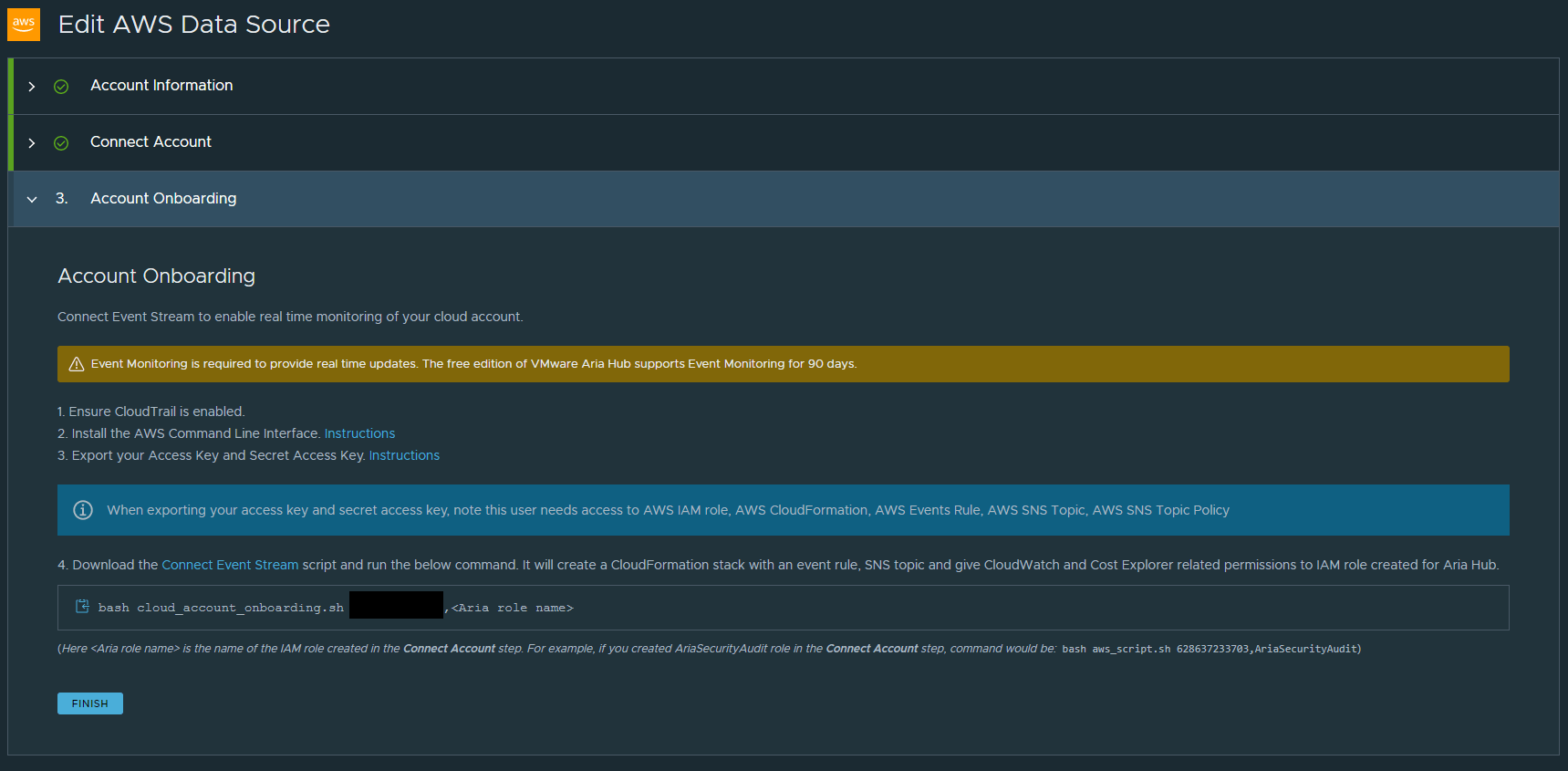
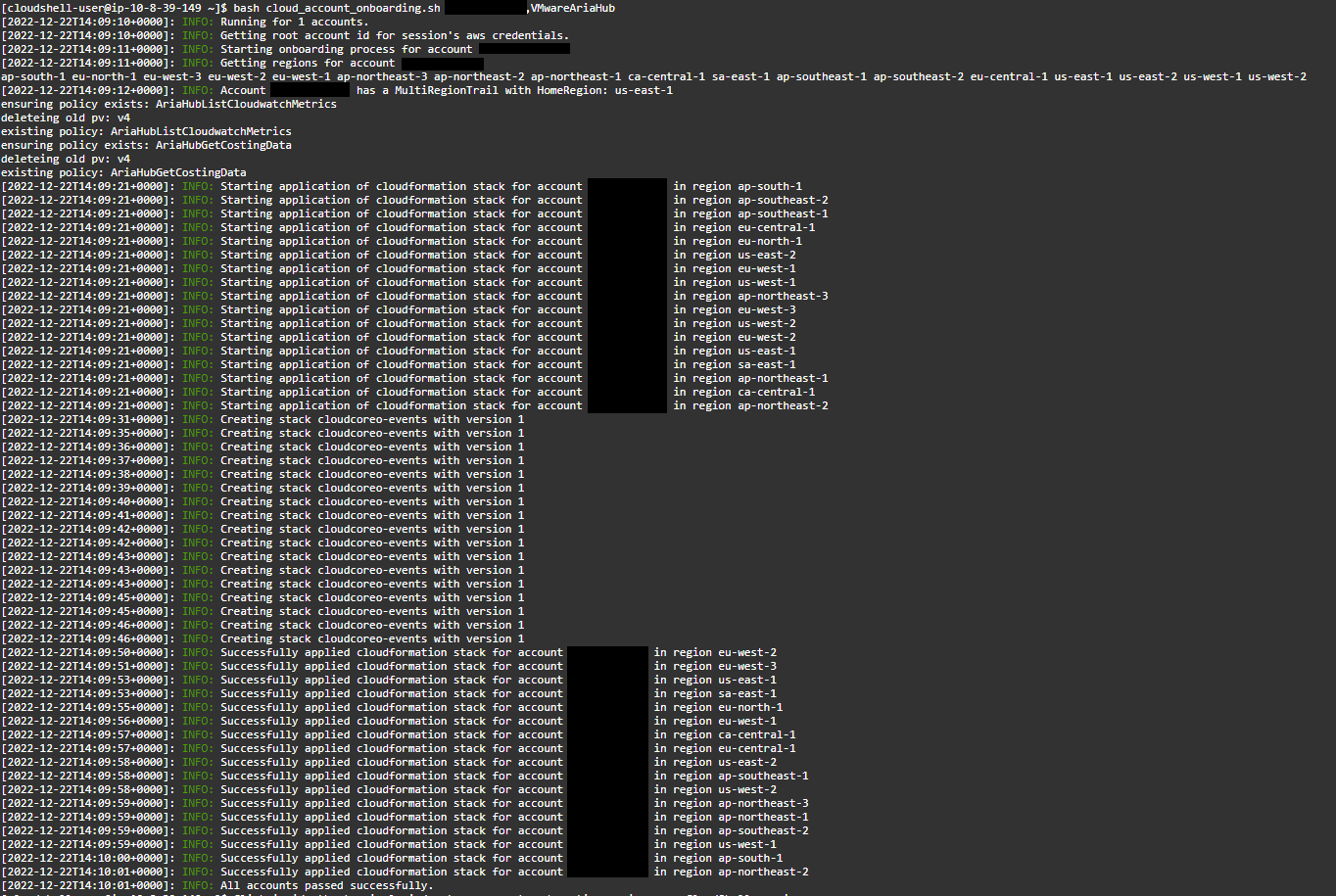
Press the link Connect Event Stream to download the .sh script. I then uploaded this to AWS CloudShell. From CloudShell I ran the command specifed: bash cloud_account_onboarding.sh <ACCOUNT_ID>,<AWS_IAM_ROLE_NAME>
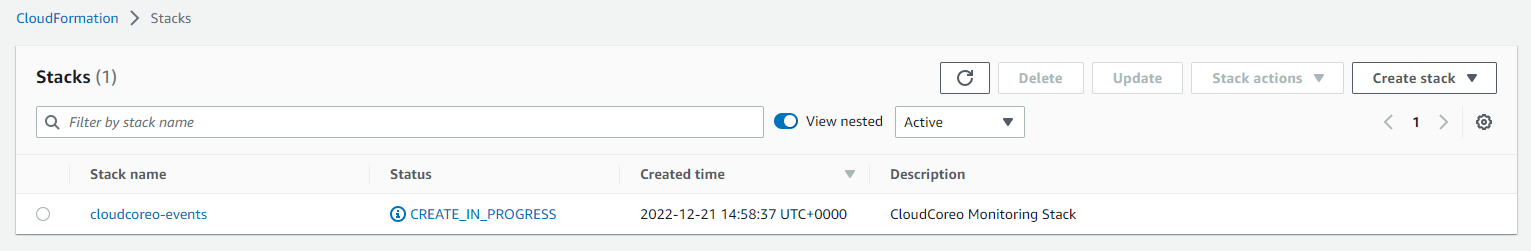
Within AWS we can see under CloudFormation the creation of a new Stack.
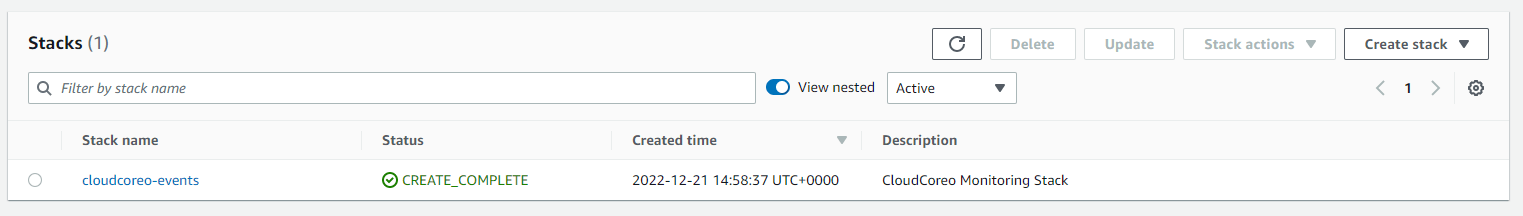
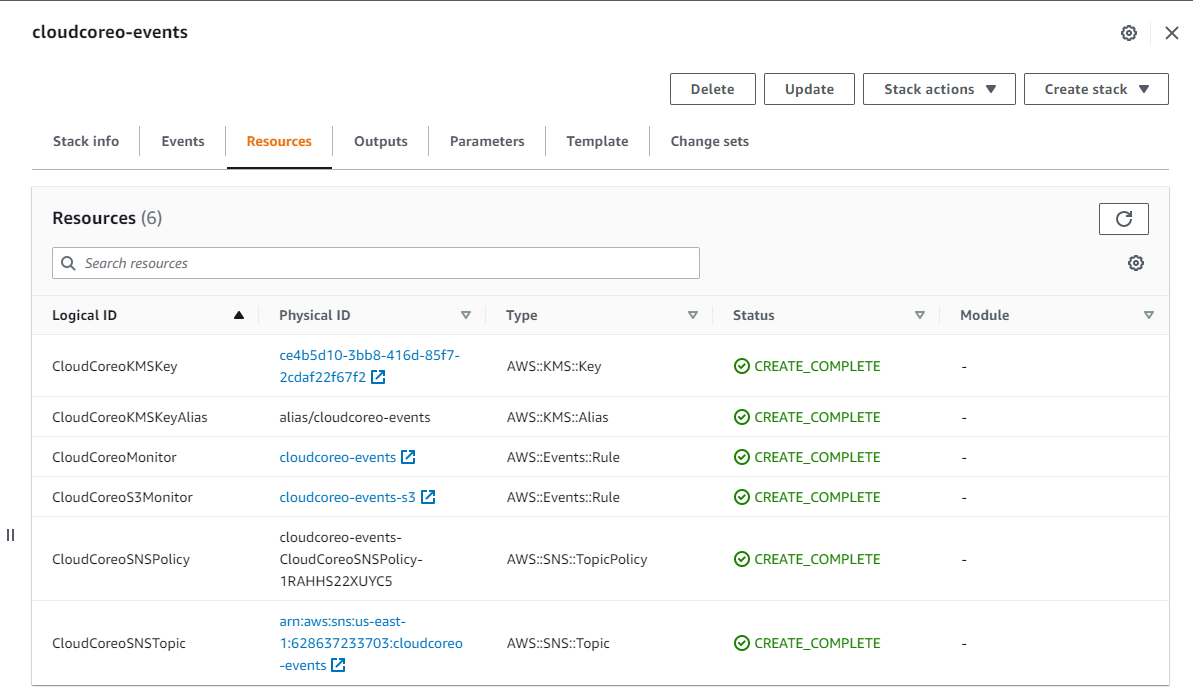
#Explore the inventory
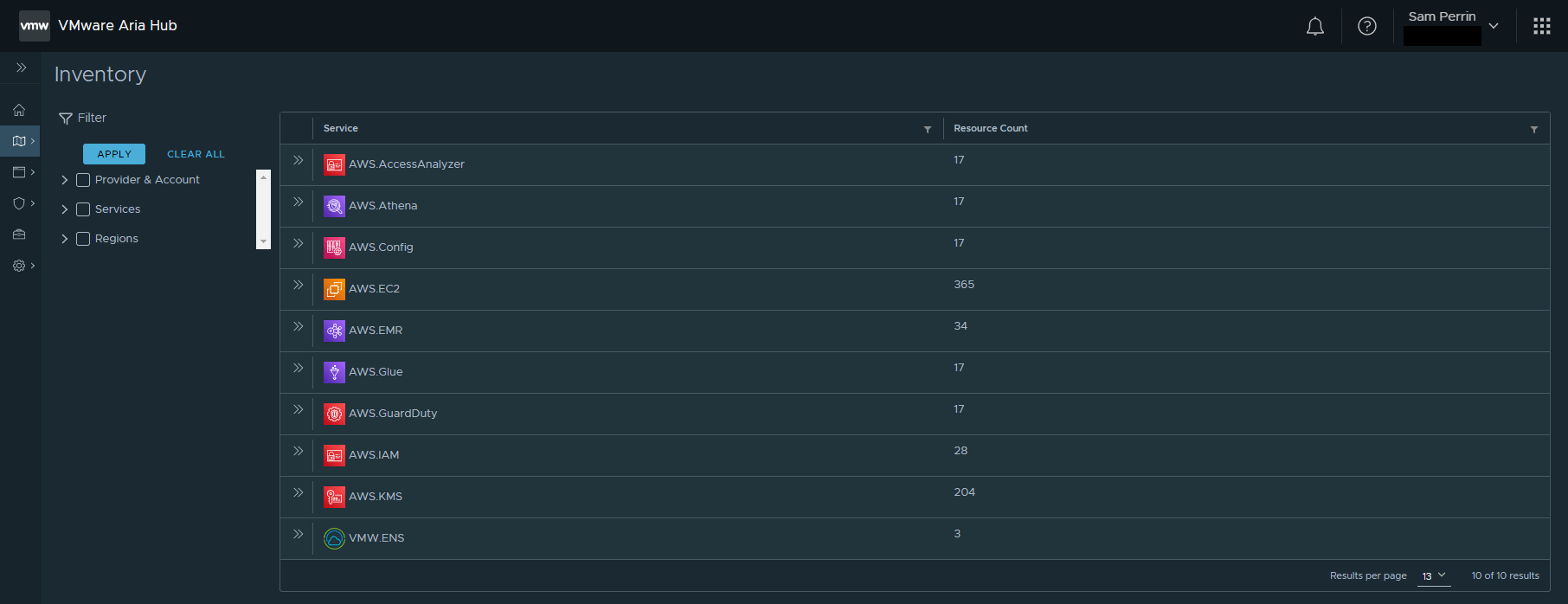
Now we have our data source connected we will start to see objects appear in our inventory. Aria Hub will start to pull in all types of inventory objects, including items that “out-of-the-box” from AWS themselevs, such as the IAM root user, EC2 network ACL’s etc. The objects are coming in from all AWS Regions.
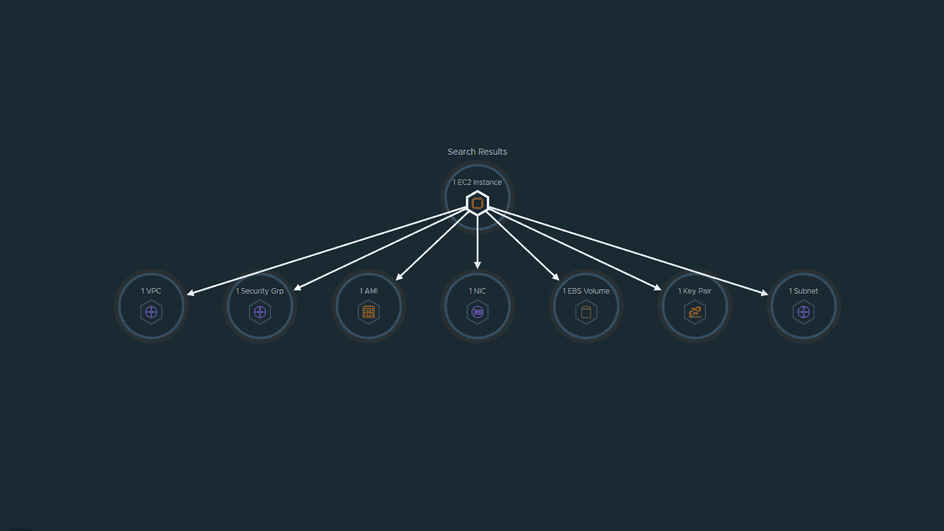
I have a single EC2 instance deployed, with the Name aria-demo and Instance ID i-069ecb9cb0e422211
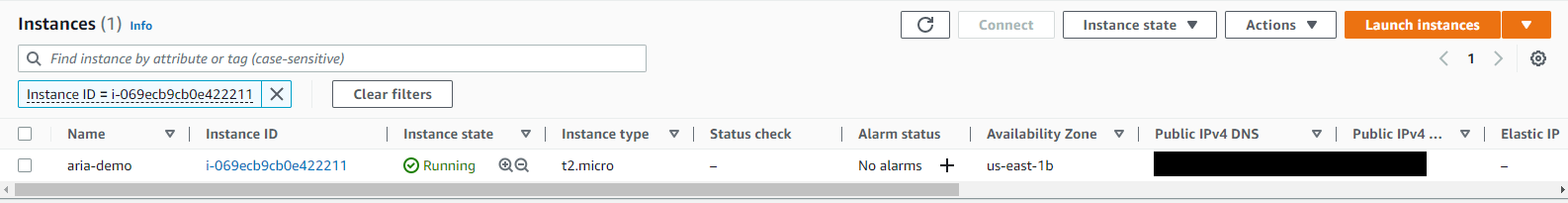
We can search for our instance in a couple of way, we can provide a generic search entityType = AWS.EC2.Instance and this will return all EC2 instances across all regions, or we can be specific and search using our Instance ID - or any of the properties attached to our EC2 instance, such as the Private IP Address.
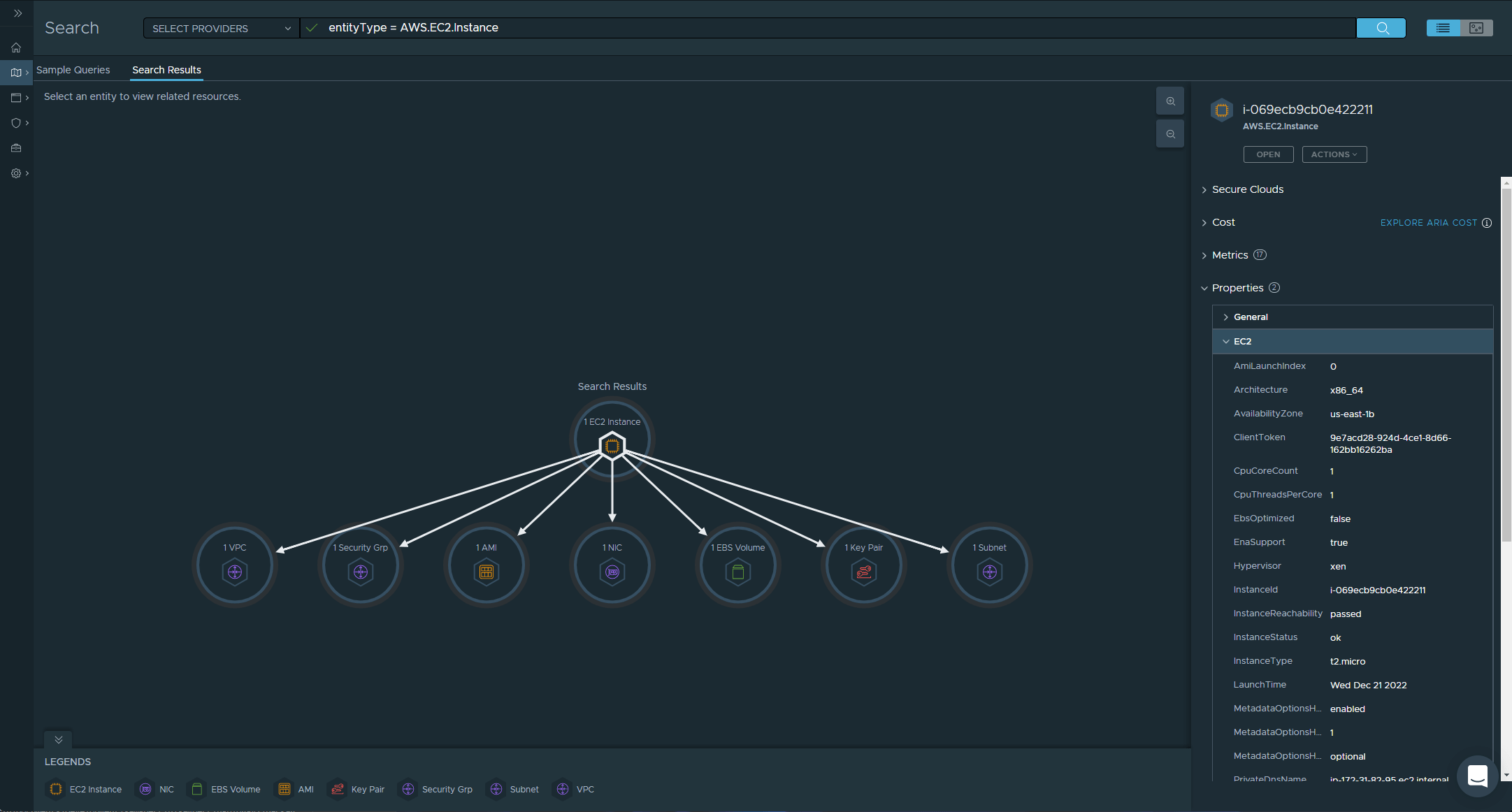
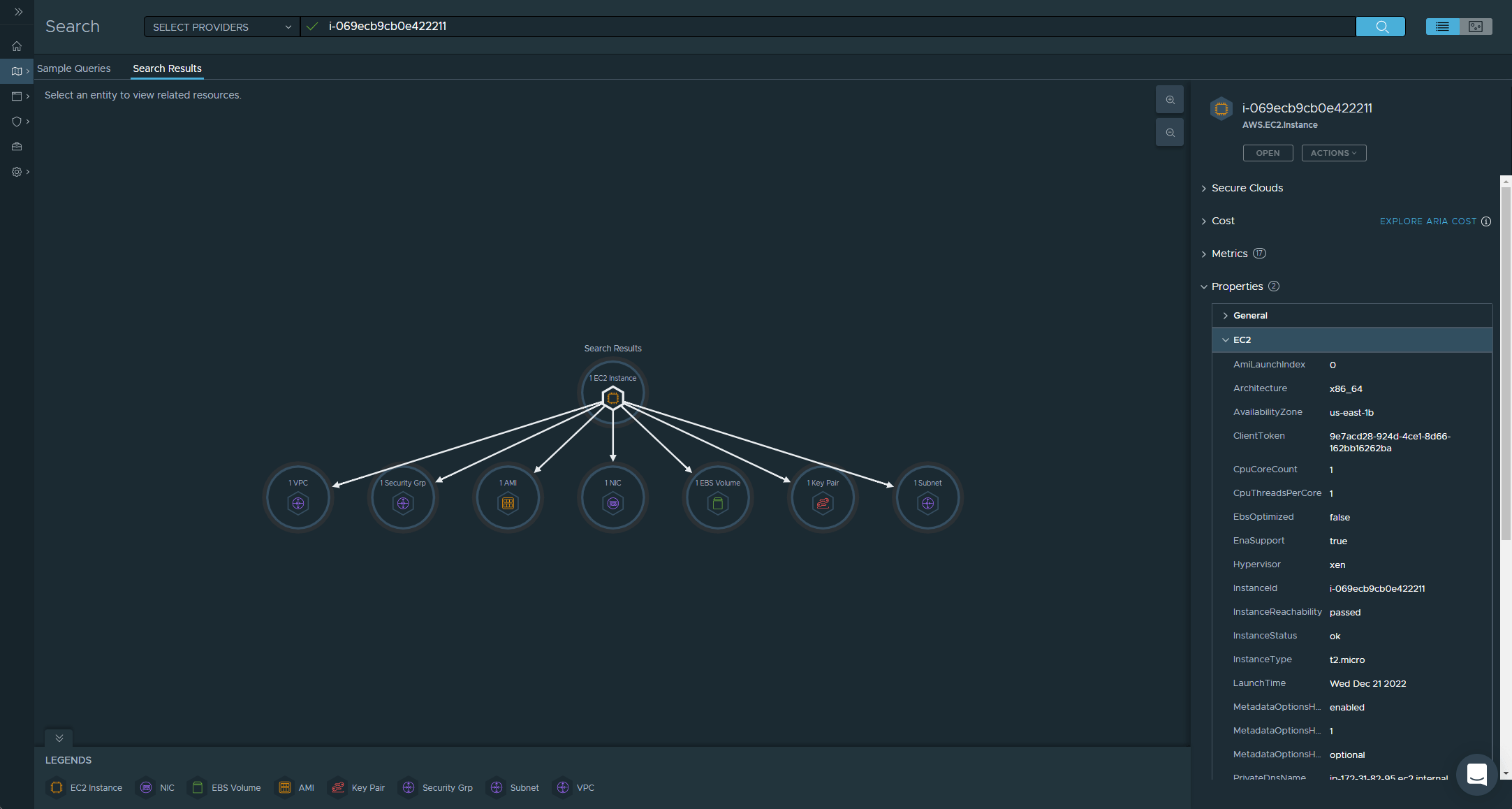
The previous two screenshots show the same result in our case, but the next two start to show how powerful Aria Hub is.
When we search by the Private IP Address, Aria Hub finds two items that match the criteria, the AWS.EC2.Instance and also the AWS.EC2.NetworkInterface. Previously the NetworkInterface was shown as a connected object, when our Search Results only returned the Instance, but now we have two search results and we have the ability to expand each of their related objects.
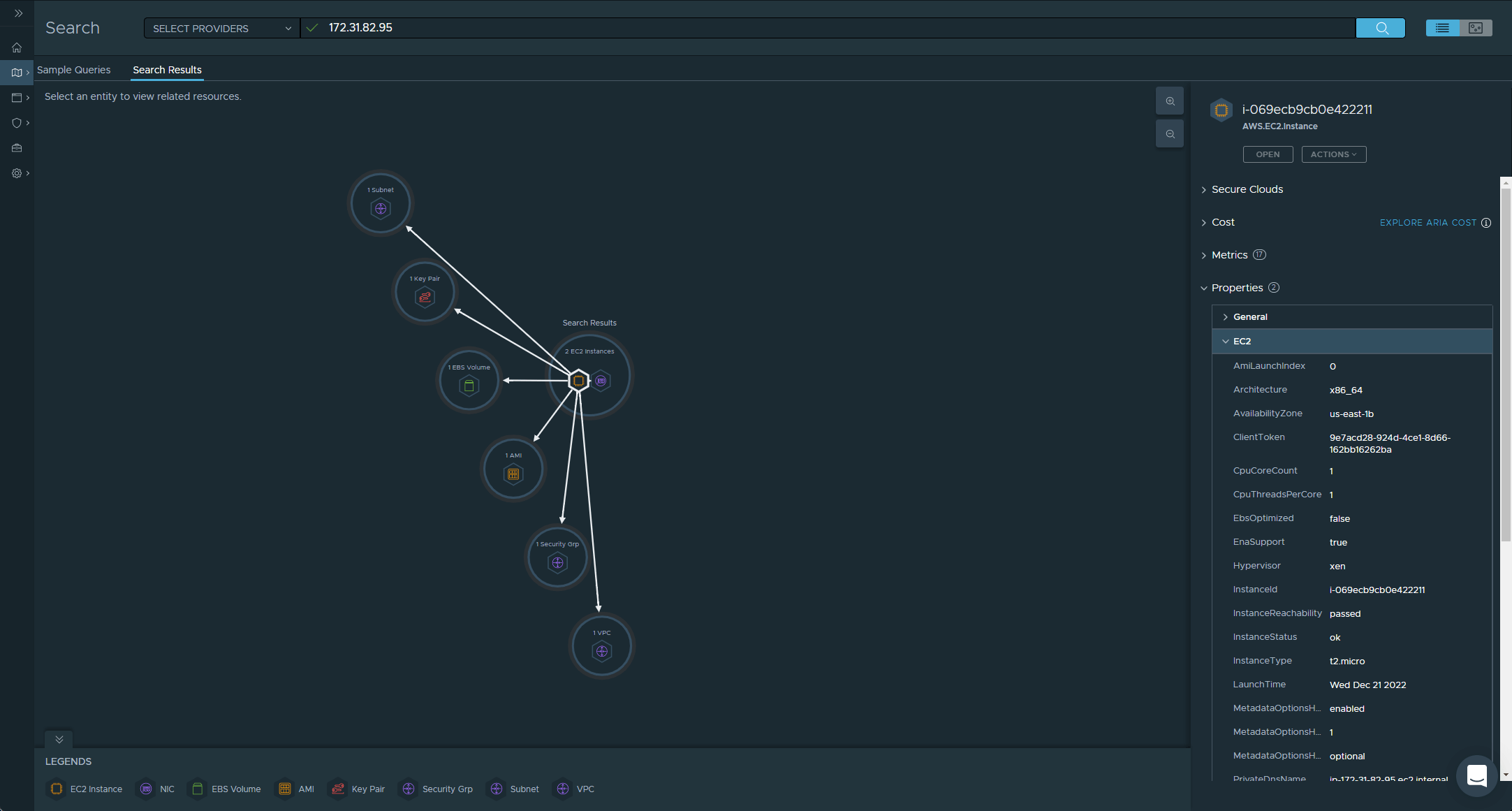
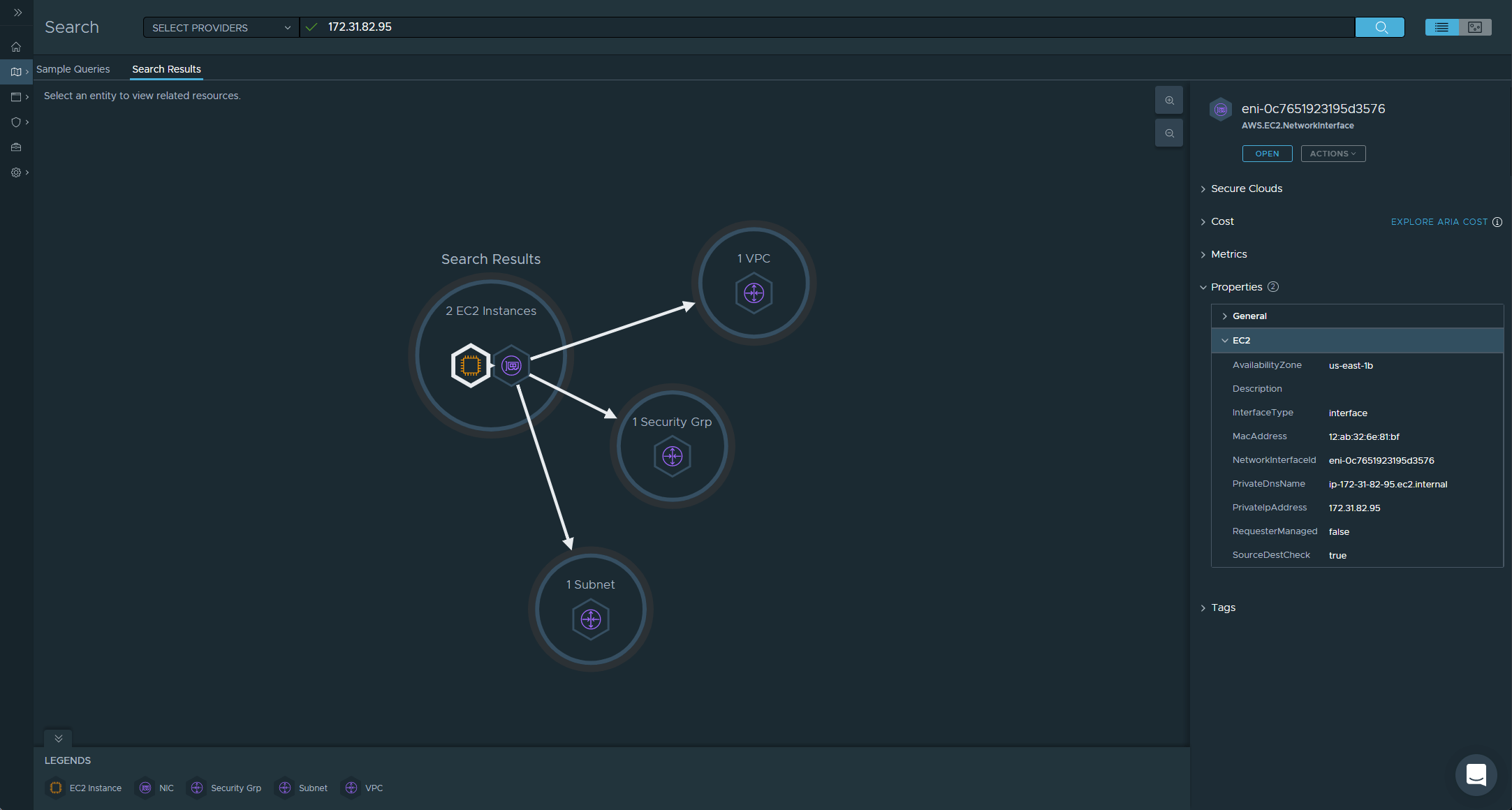
That is it for this post, we have configured our AWS Data Source and started to explore our Inventory. In our next post Exploring Aria Hub Search and GraphQL we will continue the Inventory exploration and look at the Altair portal.
#Additional
After adding my data source I noticed a warning against the Data Source: Event stream is not connected, please configure event monitoring. This is not expected behaviour and I have raised this with VMware who are investigating. At present it does not seem to be impacting my discovered Inventory.
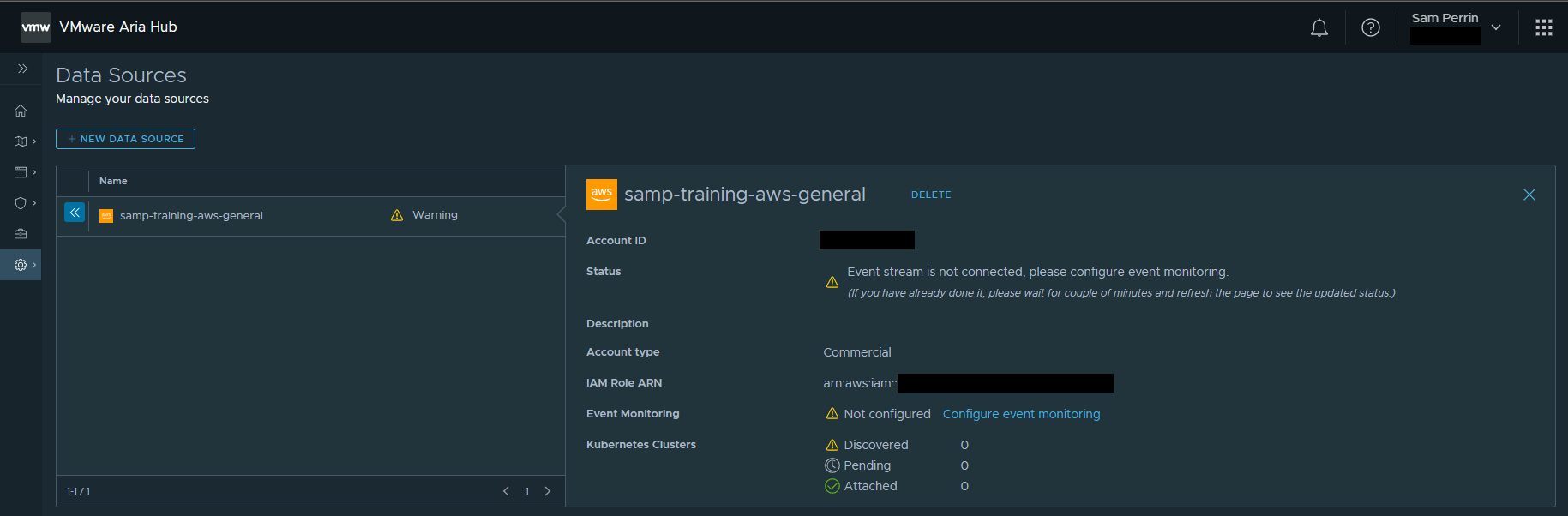
UPDATE: (23rd December 2022)
It turns out this is because Secure State was not enabled within my Organization, after claiming the invite in the Aria Hub Free Tier welcome email for Secure State (which I initially missed!) and after deleting and onboarding the data source again, I am pleased to say the connection is much happier.